As employees, we often feel that the company’s cyber-security is the responsibility of the IT team. However, there are multiple common threats to the company’s cyber-security that relate to the employee. As a result, the employee has the power to be proactive and in order to be proactive, you have to know what to look for and why your findings are important. Once you understand the common threats, you, the employee, must cultivate good habits to protect the company’s data and networks.
Social Engineering
Although the words social engineering sound technical and complicated, social engineering is defined by techtarget.com as a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. Social engineering is not technical at all, but it can apply directly to the employee and their interaction with people who try to trick them into breaking security rules. If you know the rules, know what to look for, and understand the pitfalls, you are less likely to be tricked.
A few common threats to be aware of are:
| BotnetsMalware | PharmingSpoofing | Phishing |
That probably looks like a list of foreign language words, but let’s break it down.
Botnets are largely undetected like those small spiders that hid in the crevices. They are actually software robots (bots) that build an army out of infected computers. The infected computers are known as zombies and are remote controlled by the initiator. Sounds like something from a sci-fi movie, right? Botnets send spam emails with viruses, spread malware, and use the infected computers to assist with denial of service attacks.
Typically, the IT team should be able to filter out Botnets with their security measures; however, sometimes those pesky bots manage to evade security and send spam emails and spread viruses to the employee computer. In the even this happens the employee should: 1) watch for spoofed email addresses. You can identify these addresses by noting subtle differences the sender’s name or email extension like changing a letter to a number. 2) Don’t give out personal or company information. If an email requests to verify your user name or password, go directly to the website—do not click on the link in the email. 3) Avoid strange attachments or links. Viruses and Malware can be attached to .docs, .docx, zip files, etc. If you do not recognize the email, don’t open the link. 4) Avoid the “too good to be true” emails.
You probably did not have a relative in Mumbai die and leave you a large sum of money. If you did, you certainly would not have to provide your banking information in an email in order to get funds deposited. If you think something like that is true, contact your IT team, or your lawyer.
Pharming, pronounced farming, is a scamming practice that is sometimes known as “phishing without a lure.” Pharming could be compared to a cattle herding dog. Like the herding dog guides cattle to a specific route, pharming herds multiple Internet users to bogus websites. There have been some serious pharming hi-jacks in Internet history, including an event in 2004 when a teen hijacked the eBay domain name and again in 2005, a New York ISP was redirected to a bogus site in Australia. Imagine what could happen if your company website was hijacked. The company could face serious lawsuits due to losing patient information.
You can protect yourself and your company with a little due diligence by using a trusted Internet Service Provided. Ensure the URL is spelled correctly, and make sure you and your patients who pay online are using the https rather than the standard http. In this case, the ‘S’ stands for secure. Finally, your IT team works hard to make sure security measures are in place to filter out bogus redirects.
Phishing, pronounced fishing, is an attempt to obtain user names, passwords, and credit card information. As noted above, phishing uses bait to lure you into the scam. You’ve probably seen phishing emails and did not realize it. The example below, provided by Microsoft.com, shows a typical phishing email scam.
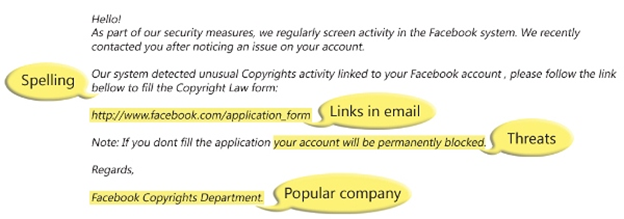
As you can see, the email has poor spelling and grammar. Professional companies and organization spend thousands of dollars to make sure their emails are error free and reflect their company professionally. Also, notice the email link. Hover over the link with your mouse. Don’t click. Look at the link. The above link looks like it is a legitimate Facebook link; however, when you hover over it, the link directs you to a different website.
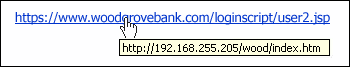
Phishing scams are not only delivered in emails, but also by telephone. These are easily avoided by refusing to click on links you are not positive of and by declining to speak to spam callers. Additionally, if you receive suspicious emails, you should report them to your IT team.
There are also malware, spam, spoofing. All of which can attack you, the end user.
Malware, a combination of the words malicious and software is a software that intends to harm your data, device, or person. A Trojan horse is a type of malware. Viruses are malware. Worms are malware.
A computer virus is similar to a biological virus. Viruses attach themselves to clean, healthy files and then spread the germ to other clean files. Like the flu, or a cold, they spread uncontrollably. Eventually making the entire computer sick. Employees should watch out for .exe (executable files) and do not run them without permission of the IT team—even if they are from another user in your network (or at your work).
Trojan horses, named after the Greek Trojan horse, are legitimate looking software or software links that hide malware. Once you let the horse into your computer, all the hidden soldiers break loose and open up breaches in your computer’s back doors to allow other malware enter. They are discreet and remain largely undetected until the damage is completed.
Worms infect the entire networks of devices either across the Internet on from your local network. They attack the first computer, then the second, and so forth. They can cost a company billions of dollars in damages. Unlike the virus that requires human interaction to spread (opening files, etc.), worms have the ability to spread automatically, worms can self-replicate, and can attach to outgoing mass emails to infect other computers.
Perhaps you are asking how to know if you have a worm? Some symptoms of a computer worm include slow performance; freezing/crashing; programs opening and running; unusual behaviors such as messages, sounds, or images; firewall warnings; strange desktop icons; sent emails you didn’t send; and operating system errors. To protect yourself from worms: keep software and computer up-to-date, avoid opening emails you don’t recognize, enable firewall and antivirus software on your computer. If you are not sure whether these measure are in place, ask your IT team. If you think you are infected, contact your IT team.
Spam is considered social engineering, but primarily occurs during email use. Most spam is delivered via botnets and contains unsolicited junk email.
Spoofing is defined by techopedia.com as a “fraudulent or malicious practice in which communication is sent from an unknown source disguised as a source known to the receiver.” Spoofing occurs most often in systems that lack a high level of security. Additionally, spoofing usually happens during email use.
Emails can be dangerous. They can cost and individual, or a company, their hopes and dreams. Email serves an important use in the work place and must be guarded, conscientiously reviewed, and sent with forethought. Because of the dominating role of email, criminals use email to commit crimes; crimes which are largely unreported and unpunished. The social engineering attacks noted above can all occur within the email setting. As a result, it pays to stay alert.
The most common access to a computer is through email or social media. Email scams include: phishing email scams, “The Nigerian Scam,” guaranteed mortgage or credit card scams, lottery scams, job offer scams, romance scams, and multiple others. According to research, in 2016 phishing scams increased 155%. The phishing scam baits the reader (win money and provide your banking information) and then steals information. If you receive a credit card or bank account alert, do not click the link. Instead go directly to your bank or credit card login page to proceed. As an employee, refrain from opening these type emails and, if you do open it, don’t click on any links. Mark as spam and notify your IT team.
As noted above, both spam and spoofing are deployed through email. Spoofing mimics a known email address or website to send malicious emails or links. Spoofing is also called nuisance emails and frequently attempts to steal personal or financial information. An example from oregonstate.edu of an email spoof is shown below.
Note there are three obvious fields that contain incorrect information:
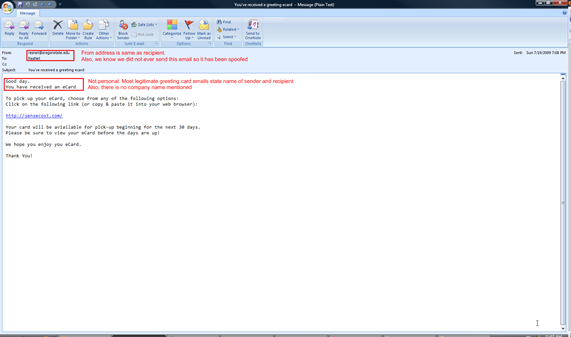
- FROM name/address
- REPLY-TO name/address
- RETURN-PATH address
There is a fourth field that is altered, but that is difficult to detect. SOURCE IP address or “X-ORIGN” address. While the other three can easily be changed inside your email program, it takes some sophisticated user knowledge to create a convincing, false IP address.
Spam on the other hand, is in your face. It is an annoyance and provides a vehicle for malware. Spammers harvest email addresses and then send out junk mail. Most of the junk mail is clearly identified, however some may think it looks interesting and click on it. A lot of spammers, use popular shopping website to get the user to look at the email. Spam email has three criteria 1) anonymity – the address and identify of the sender is not known or shown, 2) mass mailing—emails are sent to a large number of recipients, and 3) unsolicited—was not requested by the user. There may be an opt-out method noted in the email, but it rarely works. Generally, spam requests the user’s financial or personal information to gain further access to the site. This information is then used for malicious purposes.
The best way to avoid infecting your computer or risk having information stolen, is to avoid opening junk emails, emails you don’t recognize and do not click on any links or download files. It sound simple, right? Still, according to research, “more than 95% of email messages sent worldwide is believed to be spam.” (spamcop.net)
Passwords
Everyone who uses computers should use a password, a secret word or phrase that allowed the user to gain access to the computer. Most programs require certain elements are included in your password such as numbers, both capital and lower case letters, and symbols. This makes your password strong and less likely to be hacked by somebody else.
An easy method to make a strong password is to have a phrase (preferably a positive phrase) that is 10-12 characters long. For instance, the phrase ‘Smile awhile’ can be revamped into a strong password with only a few changes: $mi1@awhil6. A simple phrase using numbers and symbols in place of a few letters. Things that you might want to not use are birth dates, last names, maiden names, children names, or anything that a hacker could discover about you from social media. Also, keep separate passwords for work and home and do not share or post your password. If you have multiple account logins and passwords, you may want to consider using a password manager like LastPass Manager or a password manager of your choice.
Policy and Good Habits
Every organization has slightly different polices for email and internet use. Know your company’s policy. Know what the penalties are for policy violation. Some organizations mandate who can install/download or what can installed/downloaded. Be aware of who is responsible for company data. Employees commonly think that the IT team or corporate management has the final responsibility; but the actuality is that you, the end user has equal responsibility for the safety of your company’s data.
A good rule of thumb to incorporate is to Walk-Out, Lock-Out (WOLO). When you get up from your PC, log off. This protects you and protects your computer. In 2009, The Invisible Things lab implemented the Evil Maid Attack. It takes about one minute for an evil maid to infect your computer or laptop and is well suited for use by hotel maids, janitors and cleaning personnel, or any individual who is basically invisible in the course of the workday.
The basic concept of the Evil Maid attack is that anything can be done to a computer that is not locked out. The name comes from the idea that an attacker could infiltrate and bribe a member of the cleaning staff to compromise your computer or laptop while you are away. Typically, evil maids use a USB device with some form of key-logger (a device that records every keystroke made by a computer) to gain access to passwords and other confidential information. There are not many preventative measures to protect against an Evil Maid attack; however, WOLO when you leaving your station, having a BIOS password (check with your IT team), good physical security or an office watch (think neighborhood watch in an office setting), and finally, and try not keep sensitive data on the computer.
Keeping up with today’s threats can be a daunting task. Rely on your IT team to guide and help you. Educate yourself on common threats, empower yourself to be proactive and to protect your company’s data, and ensure that your workstation is as strong and secure as you can make it. Remember, a network is only as secure as its weakest link.